What is public DNS, what does it do, why is it so important?
November 19, 2020
Interview With Chrysostomos Psaroudakis – Creative People
December 3, 2020Increased Email deliverability is an important business need. If your email does not arrive at your customers’ or suppliers’ inboxes, then you are no longer top of mind nor part of their considerations, let alone the fact that your business purpose cannot be served in a timely manner and you are reduced to calling them to receive a reception acknowledgement.
A dialogue like this, is definitely something you have experienced being on either side.
-Did you get my email?
-No!
-Can you please check your spam folder?
-oh, I see it now….
This “I see it now”, may affect your organization’s prestige or make you lose an important deadline.
There are many reasons why emails go to recipients’ spam folders. I will try to summarize some of them.
- Lack of appropriate DNS entries on your DNS server, such as:
- SPF records
- DKIM and
- DMARC compliance issues
- Overall health of your Internet Service Provider (ISP)
- Overall health of the email server used to send out your emails
- Outgoing email volume sudden change between time periods.
We will see each one of the above in the paragraphs below.
1. Lack of appropriate DNS entries on your DNS server.
This point takes for granted that you have access to your DNS servers so as to create or update your DNS records; if you do not, then you should get access and then come back.
If you do not know what DNS does on the internet, then you should have a quick read here, before continuing.
- SPF records.
What is SPF record?
Sender Policy Framework (SPF) is an email authentication method that specifies the mail servers authorized to send email for your domain. SPF helps protect your domain from spoofing and helps ensure that your messages are delivered correctly. Mail servers that get mail from your domain, use SPF to verify that messages that appear to come from your domain, actually are from your domain.
A good way to create your own spf records is www.spfwizard.net and I suggest you combine it with mxtoolbox.com, while a good way to test those records is mxtoolbox.com.
- DKIM
DKIM (Domain Keys Identified Mail) is an authentication process that can help protect both senders and recipients from forged and phishing email. By adding DKIM signatures to your domain, recipients know that email messages actually came from users in your organization and they were not modified after they were sent.
You can create it here: tools.socketlabs.com and you can test it here: mxtoolbox.com after putting the records on your dns.
A server administrator maybe needed if you don’t have full access on it, or you are on a shared hosting environment. Even better, your hosting may have already put those records for you.
In the case of a Microsoft 365 implementation the process of creating DKIM is different as in this case, Microsoft 365 requires CNAME records instead of txt records. You can follow guidelines provided from Microsoft for that on your Office 365 portal > Admin > Exchange admin center > Protection > dkim.
In this particular scenario your test to mxtoolbox, stated above may fail, as it is looking for txt record rather than CNAME records your zones is providing. So, do not panic, you are correct, as long as Microsoft 365 admin panel states so.
- DMARC
DMARC, which stands for “Domain-based Message Authentication, Reporting & Conformance”, is an email authentication, policy, and reporting protocol. It builds on the widely deployed SPF and DKIM protocols, adding linkage to the author domain name, published policies for recipient handling of authentication failures, and reporting from receivers to senders, to improve and monitor protection of the domain from fraudulent email.
DMARC compliance is another DNS related issue whose failure can result in unsuccessful mail delivery.
You can create it here: mxtoolbox.com and you can test it here: mxtoolbox.com.
If all the above points are covered, then the chances that your mail is classified as spam become really slim. However, we have experienced issues with that when we face DNS availability issues.
To check your DNS health, you can try dnschecker.org and we suggest doing this regularly.
A friend of us, old IT Professional keeps saying:
“The root of all cause is DNS”
2.Overall health of your Internet Service Provider (ISP)
ISPs have a reputation regarding email delivery, and their reputation regarding spam is measured against UCEPROTECTL2 or UCEPROTECTL3 criteria. If you are blacklisted on the UCEPROTECTL2 / L3, then you are unlucky, as you may have an IP Address from your ISP that falls into a poor reputation range. Most of the times, the entire range of IP Addresses is blocked as a result of the fact that this provider hosts spammers. It’s a good administrator practice to check against those blacklisting criteria when your provider assigns you a new IP range or even a new static IP address. You can always refuse to accept an already blacklisted IP!
Subnet-based Blacklists are used to reject email from entire ranges of IP Addresses, i.e. providers that are hosting companies sending spam, as well as single IP Addresses that may fall in that range of IP Addresses. This blacklist type does not offer any form of manual request to delist. Your IP Address will either automatically expire from listing after a given timeframe, or after time expires from the last receipt of spam into their spam traps from your IP Address.
3. Overall health of the email server used to send out your emails
That was the part of the ISP, but you also should definitely check your email server against blacklists as part of your regular maintenance process. One of the most widespread tools to try regularly is mxtoolbox.com. In this and others, you can check whether your IP is registered on spam and other offender databases.
4. Outgoing email volume sudden change between time periods.
Hm, that is something that needs to be taken into consideration. Suppose you have no problem with your email deliverability for quite a long time, and suddenly your emails land to your recipients’ spam folders. What is wrong? You may need to check if you have a change in the volume of your outgoing emails and if you don’t have a systematic way to do that, you may check a posteriori on talosintelligence.com.
It may be a secretary sending out wishes for Christmas, or a new campaign launched from your marketing department. All domains have an average of outgoing volume and if there is a significant increase, then Talos may report it, and as other spam engines take its word for it, a chain reaction of blacklisting may come into play.
This is exactly what happens, when a computer in your network is infected with some kind of Trojan or malware that fires around to recipients around the globe. The longer the incident carries on, the wider the damage is and your IP is being listed to more and more spam registry databases.
Tough ha? It is! Email deliverability is a constant battle as many others in IT. You have to be cautious; you have to check regularly and be fast!
Increase Mailchimp deliverability
Especially for marketing purposes, many corporations utilize the MailChimp service, in order to manage mass mail sending.
A good practice would be to enable GDPR forms for your audience. For this go to audience > settings > GDPR fields and settings
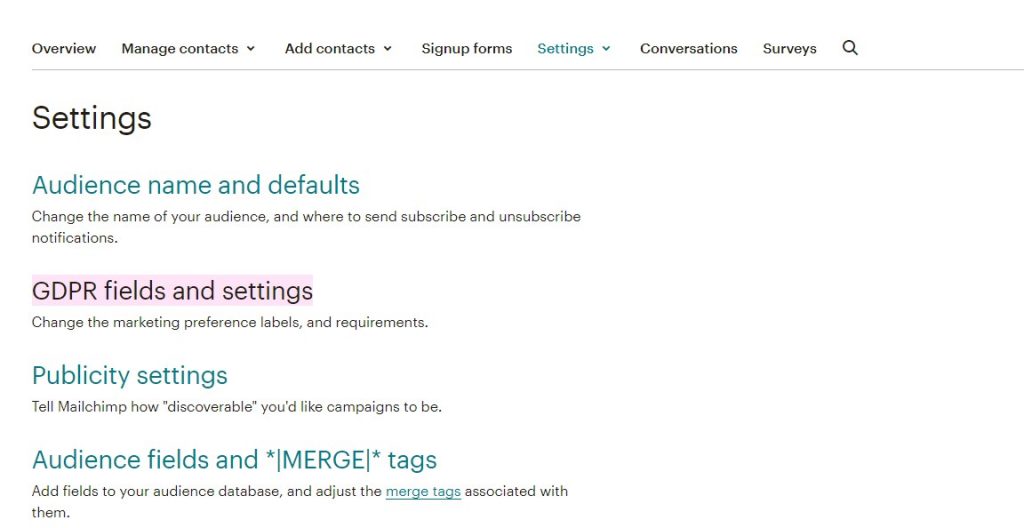
A few tips related to DNS modifications follow.
- To increase deliverability through MailChimp do not forget to:
-
- Verify and
- Authenticate your domain.
This can be found under account (top right corner) > Profile
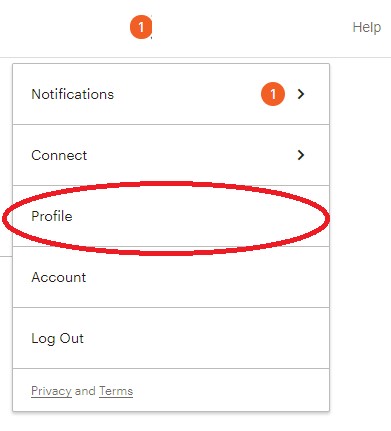
Settings > Domains
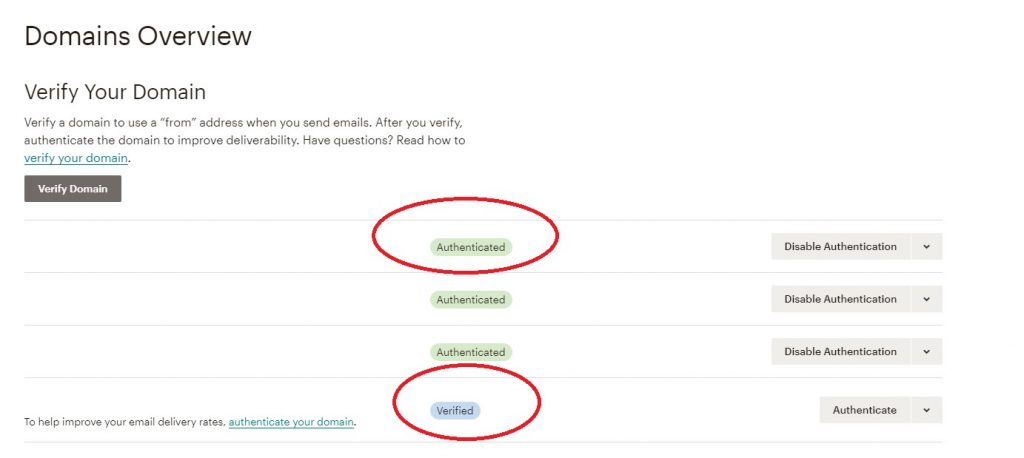
Your domain should be both verified and authenticated. Please note that in order to be authenticated it has to be verified first.
A very important thing to have in mind, when you use MailChimp for mass mail sending: No matter how hard you try, no matter how cautious you are with your DNS zone configuration, regarding spf, dkim, dmarc, etc., you will never avoid Mailchimp emails bounce on certain domains. Which (recipient) domains? The domains that strictly take into consideration your spf records.
Example: You have Office 365 deployed in your organization and if until now you had no reason altering the spf record proposed by Microsoft then your spf record would look like this
“v=spf1 include:spf.protection.outlook.com -all”
At the end you will notice a “-“. When you have this, it means that the recipient server should reject non-compliant emails, whereas when you use “~”, the recipient should accept but mark as spam.
The reason is that Mailchimp does not support SPF, as it uses its own domain in the bounce address. Their domain authentication verification tool requires including Mailchimp, though. Mailchimp always fails DMARC’s SPF alignment test because the Return-Path path does not match the “From” address. MailChimp does not support custom Return-Path (even though Mandrill, which is owned by Mailchimp, does). This makes it impossible to be 100% SPF-compliant under DMARC rules with Mailchimp.
There is one cheap trick you can do.
Before you launch and for as long as your Mailchimp campaign is running, you should switch your spf record to:
“v=spf1 include:spf.protection.outlook.com ~all”
And after your campaign ends revert it back to
“v=spf1 include:spf.protection.outlook.com -all”
Nevertheless, Mailchimp recommends SPF setup using “~all” instead of “?all”. It does not state using “–all“.